Overview
SAML allows for SSO using the Web Browser users credentials.
Noodle Prerequisites
If AD is being used, LDAP users should have already been populated within Noodle.
Quick reference
- Save your IdP URL and fingerprint in your SP (Noodle)
- Use https://yourNoodle.tld/SAML.po in your IdP settings and Web Browser.
Supported IdPs
Onelogin, Okta, and Azure
Note: Contact us for assistance integrating Other IdPs.
Noodle Configuration
In Noodle navigate to “System Tools > Settings > Single Sign-On”
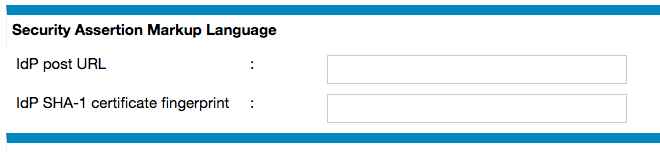
Both URL & fingerprint will be supplied by your IdP vendor. Your IdP may provide an XML file which contains the URL and certificate, to convert the certificate into a SHA-1 fingerprint there are some online SAML tools:
Format Certificate
Calculate Fingerprint
IdP Configuration
Your IdP will require a location to direct SAML responses, use https://yourNoodle.tld/SAML.po. Noodle will be compatible with the default settings of most IdPs.
OneLogin
- Navigate to "Administration > Applications > Add App"
- Search for "SAML Test Connector (IdP)"
- setting tabs
- Info (all optional)
- Configuration
- ACS (Consumer) URL Validator = .*
- ACS (Consumer) URL = https://yourNoodle.tld/SAML.po
- the rest can be left blank
- Parameters
- Configured by admin
- NameID (fka Email) = Email
- Rules (all optional)
- SSO
- X.509 Certificate = 2048-bit
- View details will show the fingerprint
- SAML Signature Algorithm = SHA-1
- SAML 2.0 Endpoint (HTTP)
- This is the URL to save in Noodle
- Access (all optional)
- Users (make sure you add some)
- Privileges (all optional)
Azure
- Azure Active Directory > Enterprise applications > New Application
- Non-gallery Application > Name can be anything > 2 Single sign on > SAML
- set "Identifier (Entity ID)" to the domain name for the Noodle instance
- set the "Reply URL" to https://yourNoodle.tld/SAML.po
- copy the "Thumbprint" and "Login URL" to put in the Noodle settings
