The Noodle application programming interface is best obtained from a running system with standard Database and Web Browser Tools, but we maintain a Noodle API static approximation by request.
Author Archives: TimL
IWA Debug
Microsoft checklist here.
Server list SPNs:
setspn -l %NoodleServiceAccount
Client list cached tickets:
klist get HTTP/%noodle.domain.tld
Client uncache tickets:
klist purge
The following information can be obtained with Wireshark;
[truncated]Authorization: Negotiate YIG...NER
GSS-API Generic Security Service Application Program Interface
OID: 1.3.6.1.5.5.2 (SPNEGO - Simple Protected Negotiation)
Simple Protected Negotiation
negTokenInit
mechTypes: 4 items
MechType: 1.2.840.48018.1.2.2 (MS KRB5 - Microsoft Kerberos 5)
MechType: 1.2.840.113554.1.2.2 (KRB5 - Kerberos 5)
MechType: 1.3.6.1.4.1.311.2.2.30 (NEGOEX - SPNEGO Extended Negotiation Security Mechanism)
MechType: 1.3.6.1.4.1.311.2.2.10 (NTLMSSP - Microsoft NTLM Security Support Provider)
mechToken: 6092a864886...
krb5_blob: 6092a864886...
KRB5 OID: 1.2.840.113554.1.2.2 (KRB5 - Kerberos 5)
krb5_tok_id: KRB5_AP_REQ (0x0001)
Kerberos
ap-req
pvno: 5
msg-type: krb-ap-req (14)
Padding: 0
ap-options: 20000000 (mutual-required)
0... .... = reserved: False
.0.. .... = use-session-key: False
..1. .... = mutual-required: True
ticket
tkt-vno: 5
realm: INTRA.NET
sname
name-type: kRB5-NT-SRV-INST (2)
sname-string: 2 items
SNameString: HTTP
SNameString: intra.net
enc-part
etype: eTYPE-ARCFOUR-HMAC-MD5 (23)
kvno: 2
cipher: 678ed5435c9ec4d6...
authenticator
etype: eTYPE-ARCFOUR-HMAC-MD5 (23)
cipher: 62a133014138848d900d436...SAML Debug
The following information can be obtained with Wireshark or with Noodle DEBUG;
https://intranet.onelogin.com/trust/saml2/http-post/sso/699546?SAMLRequest=fVLLbtsw...%2FkD&RelayState=https%3A%2F%2Fintra.net%2FSAML.poShould be sent to the IdP which before it is deflated and base 64 encoded looks like
<samlp:AuthnRequest xmlns:samlp="urn:oasis:names:tc:SAML:2.0:protocol" xmlns:saml="urn:oasis:names:tc:SAML:2.0:assertion" ID="-5abe3a1a-1671d27aa18--8000" Version="2.0" IssueInstant="2018-11-16T15:33:17Z" ProviderName="Noodle" Destination="https://intranet.onelogin.com/trust/saml2/http-post/sso/699546" ProtocolBinding="urn:oasis:names:tc:SAML:2.0:bindings:HTTP-POST" AssertionConsumerServiceURL="https://intra.net/SAML.po">
<saml:Issuer>Noodle</saml:Issuer>
<samlp:NameIDPolicy Format="urn:oasis:names:tc:SAML:2.0:nameid-format:encrypted" AllowCreate="true" />
<samlp:RequestedAuthnContext Comparison="false">
<saml:AuthnContextClassRef>urn:oasis:names:tc:SAML:2.0:ac:classes:PasswordProtectedTransport</saml:AuthnContextClassRef>
</samlp:RequestedAuthnContext>
</samlp:AuthnRequest>The IdP should reply with "Content-Type: application/x-www-form-urlencoded" containing "SAMLResponse: PHN...fCg==" which when base 64 decoded looks like
<samlp:Response xmlns:saml="urn:oasis:names:tc:SAML:2.0:assertion" xmlns:samlp="urn:oasis:names:tc:SAML:2.0:protocol" ID="R6229535893ec8f41746de8cd0bb42fe1008d88a7" Version="2.0" IssueInstant="2018-11-16T15:33:18Z" Destination="{recipient}" InResponseTo="-5abe3a1a-1671d27aa18--8000">
<saml:Issuer>https://app.onelogin.com/saml/metadata/699546</saml:Issuer>
<samlp:Status>
<samlp:StatusCode Value="urn:oasis:names:tc:SAML:2.0:status:Success" />
</samlp:Status>
<saml:Assertion xmlns:saml="urn:oasis:names:tc:SAML:2.0:assertion" xmlns:xs="http://www.w3.org/2001/XMLSchema" xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance" Version="2.0" ID="pfx95004805-783d-f0ee-f32d-17d50ca7ef90" IssueInstant="2018-11-16T15:33:18Z">
<saml:Issuer>https://app.onelogin.com/saml/metadata/699546</saml:Issuer>
<ds:Signature xmlns:ds="http://www.w3.org/2000/09/xmldsig#">
<ds:SignedInfo>
<ds:CanonicalizationMethod Algorithm="http://www.w3.org/2001/10/xml-exc-c14n#" />
<ds:SignatureMethod Algorithm="http://www.w3.org/2000/09/xmldsig#rsa-sha1" />
<ds:Reference URI="#pfx95004805-783d-f0ee-f32d-17d50ca7ef90">
<ds:Transforms>
<ds:Transform Algorithm="http://www.w3.org/2000/09/xmldsig#enveloped-signature" />
<ds:Transform Algorithm="http://www.w3.org/2001/10/xml-exc-c14n#" />
</ds:Transforms>
<ds:DigestMethod Algorithm="http://www.w3.org/2000/09/xmldsig#sha1" />
<ds:DigestValue>uCsDHp/wXNnMIz7nkq2D7OF81zY=</ds:DigestValue>
</ds:Reference>
</ds:SignedInfo>
<ds:SignatureValue>QbDsbkTMULdxYmiV8lu64jUE4BNj7ETQvUhjlgHrbaUKMaUdnluJma8T9jh8WOUEQw+Of/MGP4hMJE18f2XOJJK3X3VQnlggE5z98xjHrP0SugRH+elgQpOVkB9ht685UXtzRF6SVAIwstOGphOgqgGRwrG9fPQpN6DAKr00IOc6ItM7cbhVnA+EA8iHP8WP0n+VZXkdub9Sb/tgVkimih3/7DZPIWi6FpmlsTN88mlxBXJKnslr1Iw0ZLqLjR5dJSFz7SHrkBijirFf/kOydoQeOQrRS+6XzOmXayWCP2hHWXVvr5Ye1GbDZyjKTxMpObc+Lv6nj7llC1Mal2M0cw==</ds:SignatureValue>
<ds:KeyInfo>
<ds:X509Data>
<ds:X509Certificate>MIIEFzCCAv+gAwIBAgIUUVsi+5GzFHp5EeCzav01iiNyreEwDQYJKoZIhvcNAQEFBQAwWDELMAkGA1UEBhMCVVMxEDAOBgNVBAoMB1ZpYWxlY3QxFTATBgNVBAsMDE9uZUxvZ2luIElkUDEgMB4GA1UEAwwXT25lTG9naW4gQWNjb3VudCAxMDkzNzAwHhcNMTcwNjI1MTYzMjM5WhcNMjIwNjI2MTYzMjM5WjBYMQswCQYDVQQGEwJVUzEQMA4GA1UECgwHVmlhbGVjdDEVMBMGA1UECwwMT25lTG9naW4gSWRQMSAwHgYDVQQDDBdPbmVMb2dpbiBBY2NvdW50IDEwOTM3MDCCASIwDQYJKoZIhvcNAQEBBQADggEPADCCAQoCggEBAMFTuHcxpp8/hhD8BepAo8EI9AT7dACYFfISZo9IEcBMI1af3p/mm+lV9Iz1ZvoFTddIxHQMVe686segtdkg+p/LA+bWETyRv59yDfH8B3avZkbZkXR7lYq+noMMpQwoA3JYDcJGp9Hoh7FHuhCEZZQCGMuUbGaHMTMaMipzPB7AI9Bg6nZpTmDRqzPEd6SzKJHs18W2dZxJA+lDfze2tfyBaAuC2VFqJ3R2NZhZtpUE7IqCG67zv3ItLNk0sDqPEU3/LSIGyT0+fYcVEraBpIMkLp4MQDcihyTWZSVfhdxaOr0Fn4fUV9aTS/a1a5gybK/zat0cs6pJDgBSfoh9xRUCAwEAAaOB2DCB1TAMBgNVHRMBAf8EAjAAMB0GA1UdDgQWBBQFLDFhCLxjqc6f+cwpm7YnNZH2PTCBlQYDVR0jBIGNMIGKgBQFLDFhCLxjqc6f+cwpm7YnNZH2PaFcpFowWDELMAkGA1UEBhMCVVMxEDAOBgNVBAoMB1ZpYWxlY3QxFTATBgNVBAsMDE9uZUxvZ2luIElkUDEgMB4GA1UEAwwXT25lTG9naW4gQWNjb3VudCAxMDkzNzCCFFFbIvuRsxR6eRHgs2r9NYojcq3hMA4GA1UdDwEB/wQEAwIHgDANBgkqhkiG9w0BAQUFAAOCAQEAG/YWVdBSvyUjpO8s97Z7KPo843putSf0jgiDHtD8FGddNmdRbAwPbzWBnFupZGyPPgogoEoTRqgRalPvV0xP4PmBMJuAYssI+vwqsj9cqr4pXzpqcsGzJct8SeWSvBqbzBbu+OMbSJ5hm3RvbzSjY6nNAHY7gMe0+7V5Cd+0vzGvmSeXFnKgW7HGlP/98gmDf7KpJYmQmFDITMFc0IS0BQb13SWd7FHVchIXukqqUFFpczWx2cwUmNq1TqcGZESA3XEGbtiJ0HoEmSIQA2RLGSgEPSUgMV+UM8MhYf/bQx6VAInizM/10IokZaAQn2fzz0m5uIbf2qSMXBBoYWWWng==</ds:X509Certificate>
</ds:X509Data>
</ds:KeyInfo>
</ds:Signature>
<saml:Subject>
<saml:NameID Format="urn:oasis:names:tc:SAML:1.1:nameid-format:emailAddress">tim@intra.net</saml:NameID>
<saml:SubjectConfirmation Method="urn:oasis:names:tc:SAML:2.0:cm:bearer">
<saml:SubjectConfirmationData NotOnOrAfter="2018-11-16T15:36:18Z" Recipient="{recipient}" InResponseTo="-5abe3a1a-1671d27aa18--8000" />
</saml:SubjectConfirmation>
</saml:Subject>
<saml:Conditions NotBefore="2018-11-16T15:30:18Z" NotOnOrAfter="2018-11-16T15:36:18Z">
<saml:AudienceRestriction>
<saml:Audience>{audience}</saml:Audience>
</saml:AudienceRestriction>
</saml:Conditions>
<saml:AuthnStatement AuthnInstant="2018-11-16T15:33:17Z" SessionNotOnOrAfter="2018-11-17T15:33:18Z" SessionIndex="_c9a77760-cbdb-0136-fc65-0233ce1b6e10">
<saml:AuthnContext>
<saml:AuthnContextClassRef>urn:oasis:names:tc:SAML:2.0:ac:classes:PasswordProtectedTransport</saml:AuthnContextClassRef>
</saml:AuthnContext>
</saml:AuthnStatement>
</saml:Assertion>
</samlp:Response>
Integrated Windows Authentication (IWA)
Overview
IWA allows for SSO using the Operating System users credentials.
Prerequisites
LDAP users have been successfully populated from AD; if not please refer to the AD Configuration Guide.
Quick reference
- setspn -U -S HTTP/%noodle.domain.tld %service_account
- Add Noodle to "Microsoft Internet Explorer > Tools > Internet Options > Security > Local intranet > Sites > Advanced"
- Use https://yourNoodle.tld/SPNEGO.po
Supported configurations
Browsers
Microsoft Internet Explorer, Mozilla Firefox, Google Chrome
Note: Microsoft Edge does not support this feature.
Protocols
Kerberos in SPNEGO in GSS-API (RFC 2478)
Note: NTLM, and NegoExts are not supported.
The "Please enable the Kerberos Security Support Provider (SSP)" error indicates the wrong protocol was used.
Endpoints
AD, Azure, and F5
Note: Others may work but have not been tested
Server configuration
Define the appropriate SPN for the account which Noodle is using to bind to LDAP using one of the 4 options;
- Within the AD Users and Groups snap-in Navigate to Noodle’s service (admin) account and set the follow attribute:
- servicePrincipalName = HTTP/%noodle.domain.tld
- This may also be set via command line:
- setspn -U -S HTTP/%noodle.domain.tld %service_account
- For Windows server 2008R2 or older command line instead use
- setspn -A HTTP/%noodle.domain.tld@DOMAIN.TLD %service_account
- For AES instead of RC4
- ktpass -out noodle.keytab -mapUser NoodleServiceAccount@%DOMAIN.TLD -pass %NoodleServiceAccountPassword -mapOp set +DumpSalt -crypto AES256-SHA1 -ptype KRB5_NT_PRINCIPAL -princ HTTP/%my.noodle.tld@%DOMAIN.TLD
- Check the box "This account supports Kerberos AES 256 bit encryption" in the NoodleServiceAccount user.
Note:
- Logins from the AD Kerberos Server itself are not supported because Windows will attempt NTLM.
- Using an IP in place pf a domain name is not supported because Windows will attempt NTLM.
- For local installs, non-primary domains can be used with IWA by placing “IgnoreIWADomain = true” into noodle.properties
- Use an A record in the DNS, CNAMEs will break Kerberos
- check with
- nslookup domain.intra.net
- workaround with
- HKEY_LOCAL_MACHINE\SOFTWARE\
Microsoft\Internet Explorer\Main\FeatureControl\ FEATURE_USE_CNAME_FOR_SPN_ KB911149=true
- HKEY_LOCAL_MACHINE\SOFTWARE\
- check with
- Enable NTP services If the Noodle logs contain the following;
- .intranet,ERROR+ Caused by: KrbException: Clock skew too great (37)
Browser configuration
The next step in enabling IWA requires browser configurations to attempt authentication with the Noodle intranet website.
Once the configuration is in place users will need to access Noodle via the SPNEGO.po URL (ie. https://yourNoodle.tld/SPNEGO.po).
The following section of this guide explains this process.
Microsoft Internet Explorer & Google Chrome
Both of these browsers are configured with Microsoft Internet Explorer in "Tools > Internet Options > Security > Local intranet".
Note: If a non-default level is in use be sure “Automatic logon only in Intranet zone” is selected in "the Custom Level".
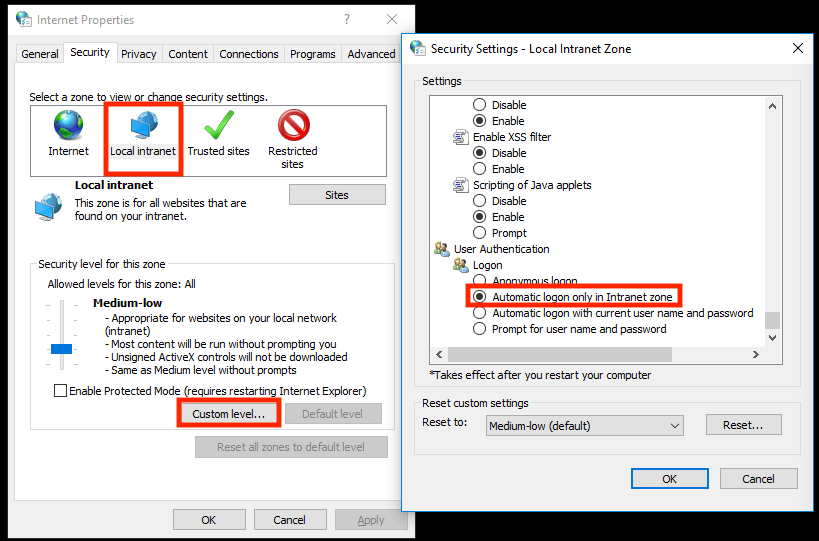
Next we will need to add the URL of your Noodle instance in "Sites > Advanced".
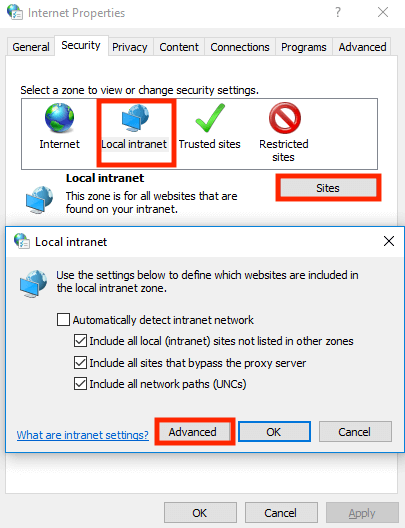
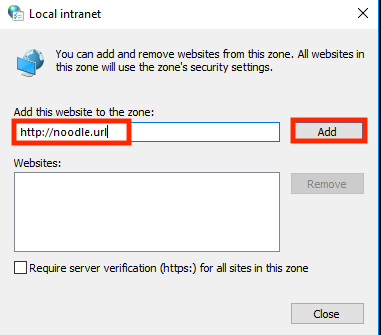
Mozilla Firefox
Enter “about:config” in the address bar, press “Enter”, and click “I Accept the Risk” when prompted.
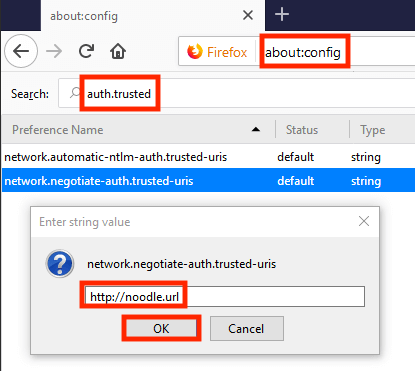
Next, search for “auth.trusted”, enter your Noodle URL in the attribute entitled “network.negotiate-auth.trusted-uris” and select OK.
At this point IWA should be fully operational for your Noodle Intranet site!
Security Assertion Markup Language (SAML)
Overview
SAML allows for SSO using the Web Browser users credentials.
Noodle Prerequisites
If AD is being used, LDAP users should have already been populated within Noodle.
Quick reference
- Save your IdP URL and fingerprint in your SP (Noodle)
- Use https://yourNoodle.tld/SAML.po in your IdP settings and Web Browser.
Supported IdPs
Onelogin, Okta, and Azure
Note: Contact us for assistance integrating Other IdPs.
Noodle Configuration
In Noodle navigate to “System Tools > Settings > Single Sign-On”
Both URL & fingerprint will be supplied by your IdP vendor. Your IdP may provide an XML file which contains the URL and certificate, to convert the certificate into a SHA-1 fingerprint there are some online SAML tools:
IdP Configuration
Your IdP will require a location to direct SAML responses, use https://yourNoodle.tld/SAML.po. Noodle will be compatible with the default settings of most IdPs.
OneLogin
- Navigate to "Administration > Applications > Add App"
- Search for "SAML Test Connector (IdP)"
- setting tabs
- Info (all optional)
- Configuration
- ACS (Consumer) URL Validator = .*
- ACS (Consumer) URL = https://yourNoodle.tld/SAML.po
- the rest can be left blank
- Parameters
- Configured by admin
- NameID (fka Email) = Email
- Configured by admin
- Rules (all optional)
- SSO
- X.509 Certificate = 2048-bit
- View details will show the fingerprint
- SAML Signature Algorithm = SHA-1
- SAML 2.0 Endpoint (HTTP)
- This is the URL to save in Noodle
- X.509 Certificate = 2048-bit
- Access (all optional)
- Users (make sure you add some)
- Privileges (all optional)
Azure
- Azure Active Directory > Enterprise applications > New Application
- Non-gallery Application > Name can be anything > 2 Single sign on > SAML
- set "Identifier (Entity ID)" to the domain name for the Noodle instance
- set the "Reply URL" to https://yourNoodle.tld/SAML.po
- copy the "Thumbprint" and "Login URL" to put in the Noodle settings
Integration
Noodle supports the following integrations:
- Authentication
- Media
 Unsplash
UnsplashYoutube
 Vimeo
Vimeo
- Files
 Google Drive (OAuth)
Google Drive (OAuth)
- Calendars (iCal)
 Google
GoogleMicrosoft
- Scripting (bash)
- email (SMTP)
 Postfix
PostfixMS Exchange
- etc
- RDBMS (SQL)
 PostgreSQL
PostgreSQLMS SQL
 MareaDB
MareaDBMySQL
CockroachDB +
 Ceph
CephOracle
- Web Browsers
Firefox
 Chromium
Chromium
- Indexing (CLI)
 TensorFlow
TensorFlowMS Office
Adobe
LibreOffice
OpenAI Whisper
Tesseract
- etc
- AI
Google Gemini
OpenAI ChatGPT
X Grok
Hugging Face
- etc
 UI Customization (JS/CSS)
UI Customization (JS/CSS)- Weather
- RSS
- etc
Configuring PostgreSQL
If you manually installed PostgreSQL it should have the following done before Noodle connects to it
- permit password authentication via 127.0.0.1 in pg_hba.conf
- run init.sql
GDPR
Local
- We hold payment information optionally provided by clients, and share it with no one. we use it to charge for our software service.
- We hold at least one pice of contact information to update payment information.
- Data is stored on our accounting computer
- This is our publicly accessible policy
- We have a DPO
- Our staff and management is aware of this document
- We use modern and up to date security.
- We appoint clients as their own representatives in the EU
- If ever we become aware of a personal data breach our customers and local authorities will be made aware.
- customers can verify and update information by simply asking.
- We review this policy annually or as required.
- We understand when DPIA is required
Hosted
- Data is stored-in / removed-from a location of the clients request.
Drive
- Create a drive key and secret
- Put them in "System Tools > Settings > General > Google Drive OAuth"
- Note that OAuth requires your Noodle server to be accessed via a public domain
- Enable in the "Administration > Properties" of the folder you want to connect.
- View the folder and follow the prompts.
Bug Bounty
Vialect Bug Bounty;
- Contact us and let us know you are interested.
- Qualification
- Confine aggressive/damaging testing to a local install
- Keep your findings confidential until the week after we fix the bug (same day we hope)
- We pay whenever we make a change as a result of your bug report.
- Send us a report with enough information for us to reproduce the bug of whatever class
- RCE Remote code execution
- EoP Elevation of privilege
- ID Information disclosure
- DoS Denial of service
- We will reward you (You will not be prosecuted)
- Public credit and thanks
- Payment (varies by severity and location of the bug up to $1,000 USD)
We thank VioPoint and All Covered for Testing Noodle.