- Upgrade
- Drive Space low
- Add more storage space (a SSD preferably) (can be done without service interruption if you are using a Logical Volume Manager)
- Out of RAM
- Add more Memory
- This warning is not yet supported for MSSQL or remote databases.
- Index Queue not empty
- Can be ignored if intermittent small numbers
- Contact support if large numbers persist
- HTTP pool too full
- in server.xml increase HTTP pools like to at least double the number of active users. (you may also have a connection per port HTTP and HTTPS)
- DB pool full
- Can be ignored if infrequent
- The default setting of 30 in noodle.properties for DatabaseManager.DB.intranet.Connection.MaxPoolSize is already fairly high so normally this is an indication that the SQL server getting slow.
- Maintenance: rebuild the indexes or upgrade the database
- If the index size is more RAM than the DB is configured to use, add more RAM
- replace spinning storage with SSD (LVMCache supports a mix).
- Increasing the number without ensuring the DB pool was filled because of volume (not latency) will likely cause out of memory or deadlock errors on the database instead of just slowness.
- Reduce load by disabling inactive users, the what's new emails, or backups during working hours.
- User limit
- Remove users from the imported Active Directory security group or contact us for a larger License.
- Additionally and optionally delete disabled users that will not be added back to the imported Active Directory security group.
System Administration
Integrated Windows Authentication (IWA)
Overview
IWA allows for SSO using the Operating System users credentials.
Prerequisites
LDAP users have been successfully populated from AD; if not please refer to the AD Configuration Guide.
Quick reference
- setspn -U -S HTTP/%noodle.domain.tld %service_account
- Add Noodle to "Microsoft Internet Explorer > Tools > Internet Options > Security > Local intranet > Sites > Advanced"
- Use https://yourNoodle.tld/SPNEGO.po
Supported configurations
Browsers
Microsoft Internet Explorer, Mozilla Firefox, Google Chrome
Note: Microsoft Edge does not support this feature.
Protocols
Kerberos in SPNEGO in GSS-API (RFC 2478)
Note: NTLM, and NegoExts are not supported.
The "Please enable the Kerberos Security Support Provider (SSP)" error indicates the wrong protocol was used.
Endpoints
AD, Azure, and F5
Note: Others may work but have not been tested
Server configuration
Define the appropriate SPN for the account which Noodle is using to bind to LDAP using one of the 4 options;
- Within the AD Users and Groups snap-in Navigate to Noodle’s service (admin) account and set the follow attribute:
- servicePrincipalName = HTTP/%noodle.domain.tld
- This may also be set via command line:
- setspn -U -S HTTP/%noodle.domain.tld %service_account
- For Windows server 2008R2 or older command line instead use
- setspn -A HTTP/%noodle.domain.tld@DOMAIN.TLD %service_account
- For AES instead of RC4
- ktpass -out noodle.keytab -mapUser NoodleServiceAccount@%DOMAIN.TLD -pass %NoodleServiceAccountPassword -mapOp set +DumpSalt -crypto AES256-SHA1 -ptype KRB5_NT_PRINCIPAL -princ HTTP/%my.noodle.tld@%DOMAIN.TLD
- Check the box "This account supports Kerberos AES 256 bit encryption" in the NoodleServiceAccount user.
Note:
- Logins from the AD Kerberos Server itself are not supported because Windows will attempt NTLM.
- Using an IP in place pf a domain name is not supported because Windows will attempt NTLM.
- For local installs, non-primary domains can be used with IWA by placing “IgnoreIWADomain = true” into noodle.properties
- Use an A record in the DNS, CNAMEs will break Kerberos
- check with
- nslookup domain.intra.net
- workaround with
- HKEY_LOCAL_MACHINE\SOFTWARE\
Microsoft\Internet Explorer\Main\FeatureControl\ FEATURE_USE_CNAME_FOR_SPN_ KB911149=true
- HKEY_LOCAL_MACHINE\SOFTWARE\
- check with
- Enable NTP services If the Noodle logs contain the following;
- .intranet,ERROR+ Caused by: KrbException: Clock skew too great (37)
Browser configuration
The next step in enabling IWA requires browser configurations to attempt authentication with the Noodle intranet website.
Once the configuration is in place users will need to access Noodle via the SPNEGO.po URL (ie. https://yourNoodle.tld/SPNEGO.po).
The following section of this guide explains this process.
Microsoft Internet Explorer & Google Chrome
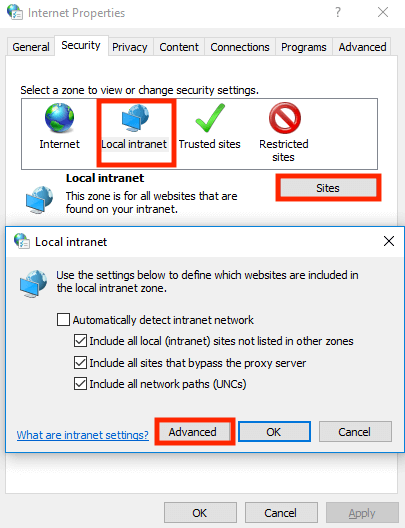
Both of these browsers are configured with Microsoft Internet Explorer in "Tools > Internet Options > Security > Local intranet".
Note: If a non-default level is in use be sure “Automatic logon only in Intranet zone” is selected in "the Custom Level".
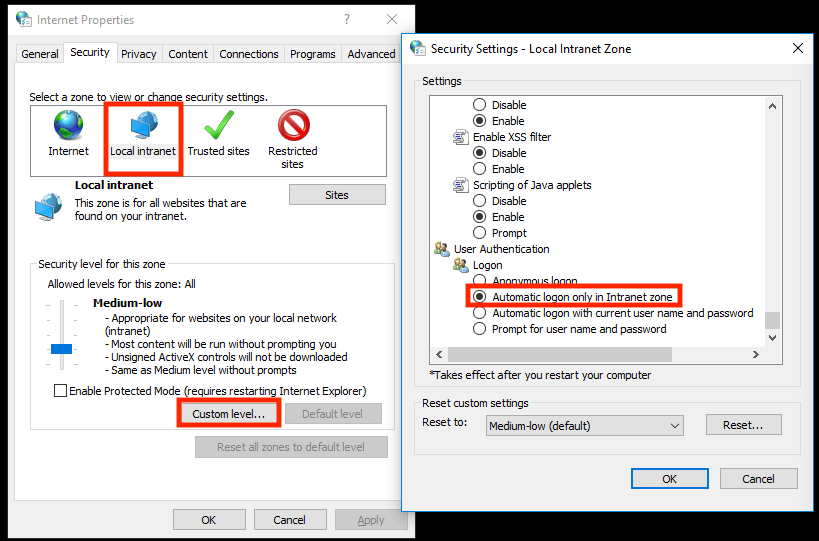
Next we will need to add the URL of your Noodle instance in "Sites > Advanced".
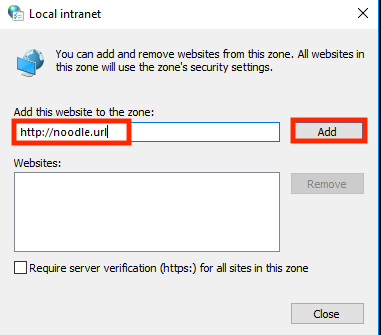
Mozilla Firefox
Enter “about:config” in the address bar, press “Enter”, and click “I Accept the Risk” when prompted.
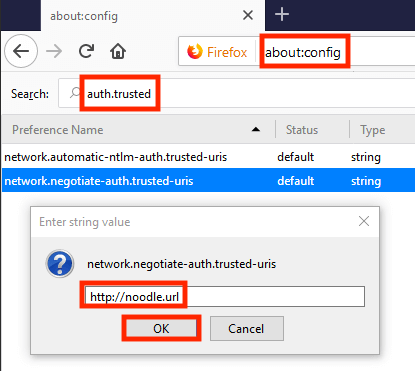
Next, search for “auth.trusted”, enter your Noodle URL in the attribute entitled “network.negotiate-auth.trusted-uris” and select OK.
At this point IWA should be fully operational for your Noodle Intranet site!
Configuring PostgreSQL
If you manually installed PostgreSQL it should have the following done before Noodle connects to it
- permit password authentication via 127.0.0.1 in pg_hba.conf
- run init.sql
postgresql.conf
postgresql.conf ships with quite modest defaults so be sure to august it for anything more than light use. We recommend for ~4k users;
- Available Memory = System Memory - OS (1GB for Windows) - Java (100 to 512)
- effective_cache_size = Available Memory / 2
- shared_buffers = effective_cache_size / 4
- max_locks_per_transaction = 512
- max_connections = 60
- checkpoint_segments 30
- log_min_duration_statement = 10000
- log_line_prefix = ''%m: ''
There is a convenient config creator here.
Random
The first encrypted request after starting Noodle can be 3 orders of magnitude slower than normal due to random entropy pool depletion. If your server suffers from this issue (most EC2 servers) you can verify by checking the pool size:
cd /proc/sys/kernel/random/ && cat poolsize entropy_avail
There are at least 3 solutions to a depleted pool:
1 Hardware
Some hardware includes random generators (like the rdrand CPU flag):
grep -ic rdrand /proc/cpuinfoYou can enable its use with:
Debian/Ubuntu
apt install rng-tools
systemctl start rng-tools.service
systemctl enable rng-tools.serviceFedora/RedHat
yum install rng-tools
systemctl start rngd.service
systemctl enable rngd.service2 urandom
If you don't have a hardware generator or you don't trust it you can edit /opt/Noodle/multiserver to use:
-Djava.security.egd=file:///dev/urandomOr edit java.security in $JRE8/lib/security or $JRE9/conf/security to use:
securerandom.source=file:/dev/urandom3 haveged
For higher throughput and lower CPU usage than urandom haveged can be used but it can still block:
Debian/Ubuntu
apt install haveged
systemctl start haveged.service
systemctl enable haveged.serviceFedora/RedHat
yum install haveged
systemctl start haveged.service
systemctl enable haveged.servicepem to pfx
openssl pkcs12 -export -in public.pem -inkey private.pem -out noodle.pfx -name domain.tld -CAfile chain.pem -caname root -chainCentOS 7.2 install example
#Helpers
yum install -y epel-release
yum install -y bc ntp.x86_64 screen tree catdoc id3lib html2text unrtf p7zip-plugins.x86_64 libjpeg-turbo.x86_64 poppler-utils unzip.x86_64 netpbm-progs.x86_64 perl-Image-ExifTool.noarch postgresql-server.x86_64 postgresql-contrib.x86_64 java-11-openjdk.x86_64;
rpm -Uvh http://li.nux.ro/download/nux/dextop/el7/x86_64/nux-dextop-release-0-5.el7.nux.noarch.rpm;
yum install -y ffmpeg;
newcfg (){
F="$1"
chown --reference="$F" "$F".new
chmod --reference="$F" "$F".new
mv -f "$F".new "$F"
}
#PostgreSQL
/usr/bin/postgresql-setup initdb
chkconfig --level 235 postgresql on
TMP=/var/lib/pgsql/data/pg_hba.conf
cp $TMP $TMP.original
cat $TMP | grep -vP "^ *host.*127" > $TMP.new
echo -e "host\tall\tall\t127.0.0.1/32\tpassword" >> $TMP.new
newcfg $TMP
TMP=/var/lib/pgsql/data/postgresql.conf
cp $TMP $TMP.original
MT=$(cat /proc/meminfo | grep MemTotal | perl -pe 's/^[^ ]* *([0-9]+) *kB$/$1\/1000/g');
#java+linux=(512+256)
ECS=$(echo "($MT-(512+256))/2" | bc);
SB=$(echo "($MT-(512+256))/4" | bc);
cat $TMP | perl -pe 's/^#?(effective_cache_size)[ \t]*=[ \t]*[^ \t]+([ \t].*)?$/$1 = '$ECS'MB$2/g' \
| perl -pe 's/^#?(shared_buffers)[ \t]*=[ \t]*[^ \t]+([ \t].*)?$/$1 = '$SB'MB$2/g' \
| perl -pe 's/^#?(max_locks_per_transaction)[ \t]*=[ \t]*[^ \t]+([ \t].*)?$/$1 = 512$2/g' \
| perl -pe 's/^#?(max_connections)[ \t]*=[ \t]*[^ \t]+([ \t].*)?$/$1 = 60$2/g' \
| perl -pe 's/^#?(checkpoint_segments)[ \t]*=[ \t]*[^ \t]+([ \t].*)?$/$1 = 30$2/g' \
| perl -pe 's/^#?(log_min_duration_statement)[ \t]*=[ \t]*[^ \t]+([ \t].*)?$/$1 = 30000$2/g' \
| perl -pe 's/^#?(log_line_prefix)[ \t]*=[ \t]*[^#]+(#.*)?$/$1 = '\''%m: '\''\t\t$2/g' \
> $TMP.new
newcfg $TMP
service postgresql start
#Noodle (first take note of your available ram and java location)
tar -zxf ./Noodle.tar.gz
su postgres -c 'cd ~/;/usr/bin/psql -d postgres -U postgres --file /opt/Noodle/init.sql'
cd ./Noodle
cp noodle.daemon /etc/init.d/noodle
chkconfig --add noodle
chkconfig --levels 235 noodle on
service noodle start
Remember to permit traffic through your remote and local firewalls.
firewall-cmd --add-service=http
firewall-cmd --runtime-to-permanentOther Linux Installation examples available.
CentOS 6.7 install example
(see also latest version howto and version notes)
ssh root@my.server.tld
###########################################################
##postgres
yum install postgresql postgresql-server postgresql-server postgresql-contrib
chkconfig --level 235 postgresql on
service postgresql start
vim /var/lib/pgsql/data/pg_hba.conf
# 127.0.0.1/32 password
vim /var/lib/pgsql/data/postgresql.conf
# maintenance_work_mem=128000
# autovacuum = on
service postgresql restart
su postgres
pgsql -U postgres
CREATE LANGAUGE plpgsql;
CREATE DATABASE noodledb WITH ENCODING = 'UNICODE';
create user noodleuser with superuser password 'some long password';
GRANT ALL PRIVILEGES ON DATABASE noodledb to noodleuser;
\q
exit
###########################################################
##java (get an updated url from java.sun.com)
cd /opt
wget 'http://javadl.oracle.com/webapps/download/AutoDL?BundleId=207765' -O jre.tar.gz
tar -zxf jre.tar.gz
rm -f jre.tar.gz
###########################################################
##7z
# you can use yum-priorities and rpmforge or you can do it from source
yum install p7zip p7zip-plugins
# you might need to make a link from 7z to 7z[ar] for "which 7z" to work
###########################################################
##Noodle
wget somewhere/Noodle.tar.gz
tar -xvvf ./Noodle.tar.gz
cd ./noodleOther Linux Installation examples available.
Ubuntu 16.04 install example
sudo -i
apt update
apt -y upgrade
apt -y dist-upgrade
apt install -y postgresql-contrib tree p7zip-full sysstat catdoc antiword html2text unrtf libid3-tools ffmpeg openjdk-8-jre poppler-utils unzip
cd /opt
tar -xf ./Noodle.tar.gz
cd ./Noodle
su postgres -c 'cd ~/;psql --file /opt/Noodle/init.sql'
mv noodle.daemon /etc/init.d/noodle
update-rc.d noodle defaults
service noodle start
Other Linux Installation examples available.
Ubuntu 14.04 install example
(see also howto get a new version of PGSQL )
sudo -i
apt-get install -y postgresql-9.3 postgresql-contrib-9.3 default-jre p7zip-full screen
cd /opt
tar -xf ./Noodle.tar.gz
cd ./Noodle
echo "host all all 127.0.0.1/32 password" >> /etc/postgresql/9.3/main/pg_hba.conf
service postgres start
su postgres -c 'cd ~/;psql --file /opt/Noodle/init.sql'
mv noodle.daemon /etc/init.d/noodle
service noodle start
update-rc.d noodle defaults
Other Linux Installation examples available.